Revolutionizing Data Protection in a Agentic world
BillionAPIs pioneers intelligent data protection for enterprise API pathways. Our AI-driven platform continuously learns, identifies, and protects your sensitive data as it flows through APIs. We prevent data exfiltration and data poisoning without impacting business continuity.
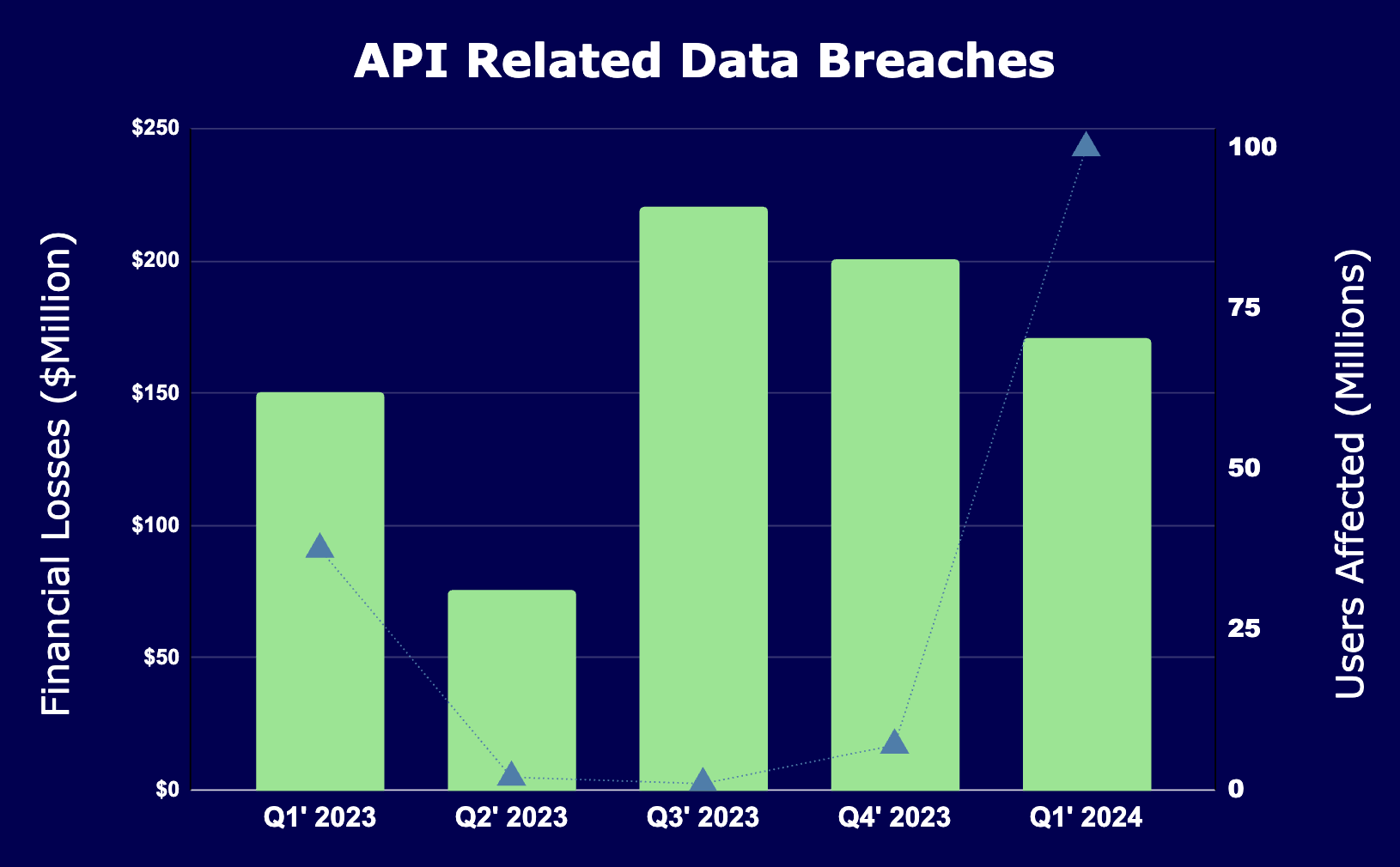
Data Exposure: The Invisible Threat
Your most valuable asset is one breach away from catastrophe. Unchecked data access isn't just a risk—it's an open invitation to a bigger disaster.
Limitations of current tools
Limited Visibility
Data in motion, across hybrid environments and diverse identities; needs end-to-end visibility.
Complex and Static Data Pathways
Robust protection become difficult as data crosses enterprise boundaries, which are always-on, and potential attack surfaces.
Lack of Proactive protection
Breaches go undetected for months within your enterprise pathways, making remediation expensive and time-consuming.

1
Limited Visibility
Data in motion, across hybrid environments and diverse identities; needs end-to-end visibility.
2
Complex and static data pathways
Robust protection become difficult as data crosses enterprise boundaries, which are always-on, and potential attack surfaces.
3
Lack of proactive protection
Breaches go undetected for months within your enterprise pathways, making remediation expensive and time-consuming.
How it works
Introducing Data Identity
We've cracked the code on data protection. Our AI-powered Data Identity technology assigns a unique identity to your sensitive data as it moves through APIs—on ingress or egress. No more blind spots.
No more data theft. No more toxic infiltrations. Complete visibility, complete control.

01. Assign Every Data Object with a Unique Identity
- Ensure every data object is given a distinct identifier.
- This identity will allow easy tracking and management of data assets.
02. Ensure Their Privilege Level is Set Correctly
- Define and assign privilege levels based on the role and purpose of each data object.
- Regularly audit permissions to ensure accuracy and compliance.
03. Access Protection Moves with the Data Identity
- Implement protection mechanisms that stay with the data, even when it transitions across systems.
- Use identity-based security measures to prevent unauthorized access.
04. Observe and Protect Your Data-in-Motion Against Any Breaches
- Monitor data as it moves across systems, ensuring its integrity and confidentiality.
- Employ encryption and real-time monitoring tools to detect and address potential breaches.
New Approach with BillionAPIs

Protect Data-in-motion
End-to-end ingress and egress data protection across API pathway with full encryption.

Reduce attack surface
Cut down long duration API sessions with ephemeral gateways.

Detect breaches in real-time
Tarpit threat vectors with lightweight AI-based copilots, complete with responses.
